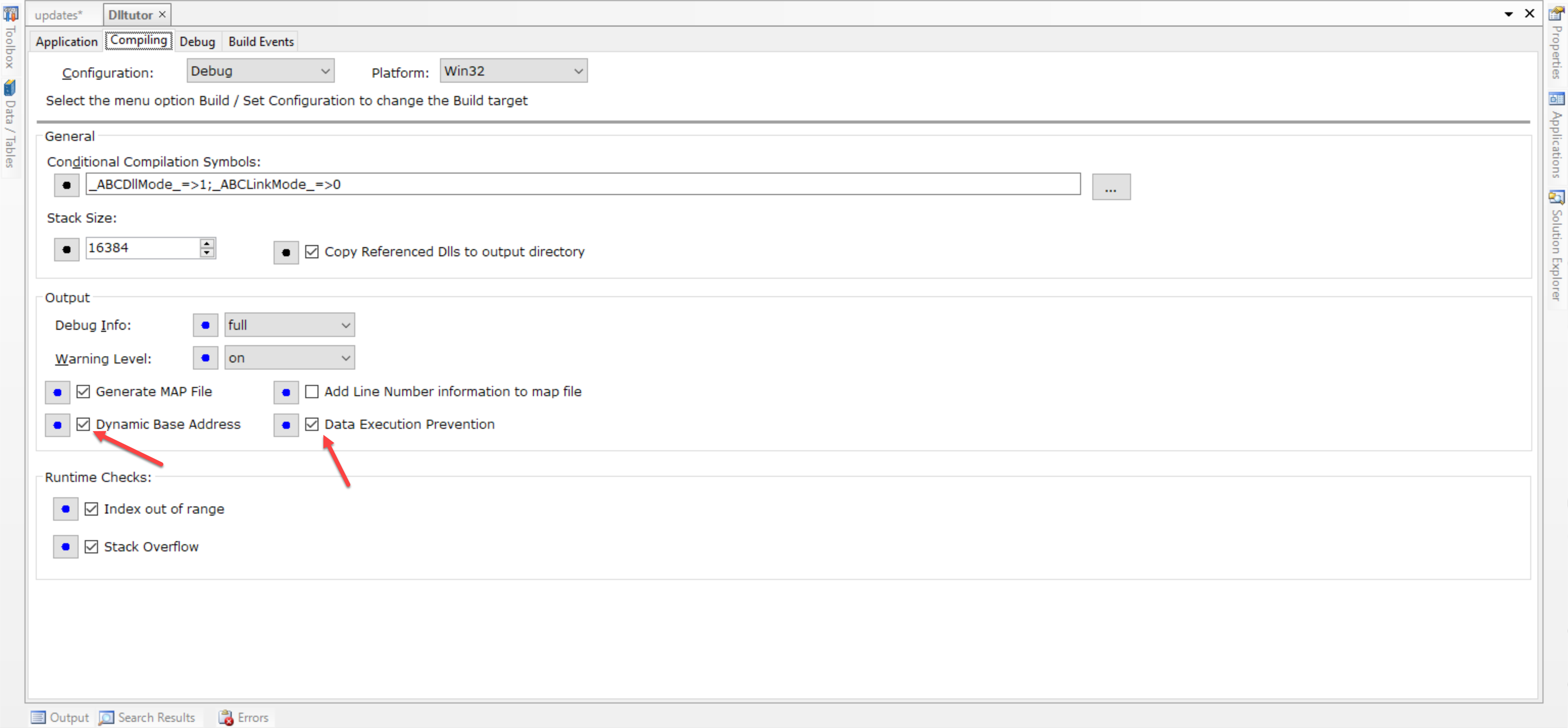
We’ve added two new linker options that can make your applications more secure from malware exploits; ASLR (Address space layout randomization) and DEP (Data Execution Prevention).
ASLR (Address space layout randomization)
ASLR also often referred to as DYNAMICBASE, modifies the header of an executable to indicate whether the application should be randomly rebased at load time by the OS.
ASLR is transparent to your application. With ASLR, the only difference is the OS will rebase the executable unconditionally, instead of doing it only when a base image conflict exists. ASLR is supported only on Windows Vista and later operating systems, it is ignored on older OS versions.
Why should you use ASLR? On platforms without ASLR support (versions of Windows prior to Windows Vista), there is a well know exploit approach for an attacker to find and manipulate code that exists within its modules (DLLs and EXEs) when the modules have been loaded at predictable locations in the address space of the process. Address space layout randomization (ASLR) randomizes the memory locations used by programs, making it much harder for an attacker to correctly guess the location of a given process, including the base of the executable and the positions of the stack, heap and libraries.
In the next build of C11, the “Dynamic Base Address” option is set on by default at the project level.
If you want to set it from the EXP file, the command is:
DYNAMIC_BASE
on any line by itself (outside of the Exports)
DEP (Data Execution Prevention)
The purpose of DEP is to prevent attackers from being able to execute data as if it were code. This stops an attack that tries to execute code from the stack, heap, and other non-code memory areas. DEP prevents malware from writing code into data pages then executing it.
In the next build of C11, the “Data Execution Protection” option is set on by default at the project level.
If you want to set it from the EXP file, the command is:
DEP
on any line by itself (outside of the Exports)
Summary
The combined use of DEP (Data Execution Prevention) and ASLR (Address Space Layout Randomization) have proven to be effective against the types of exploits that are in use today. DEP breaks exploitation techniques that attackers have traditionally relied upon, but DEP without ASLR is not sufficient to prevent arbitrary code execution in most cases. DEP is also needed to make ASLR (Address Space Layout Randomization) more effective.
Adding these two malware countermeasures to your applications is especially useful for applications that handle financial data, credit cards, health info, and more.
To set these linker options in Clarion at the Project level:
Open the Project properties page: en
en
then click on the “Compiling” tab and set the checkboxes to ON